Latest Blogs

How to find Data Leaks For Free
How to Search For Data Leaks For Free. Get hold of the username, email or phone of the person you want to search. In my experience, the former two have a higher success rate. It is only for Educational Purposes. Don't Misuse it. There is only chance of Finding password was 70%.
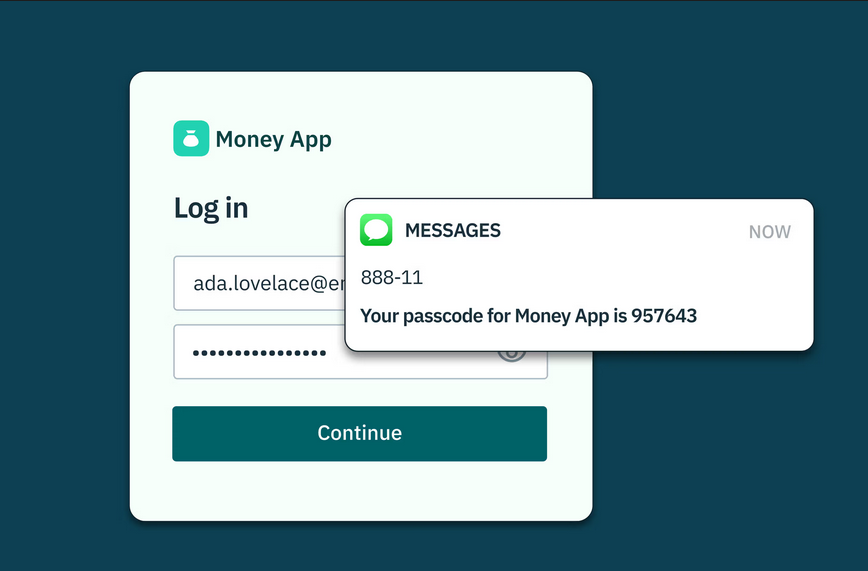
OTP ByPass Method
One-Time Passwords (OTP) are commonly used for authentication and verification in account registration, login, and critical actions. However, poor OTP implementations can lead to authentication bypass, account takeover, and unauthorized access.
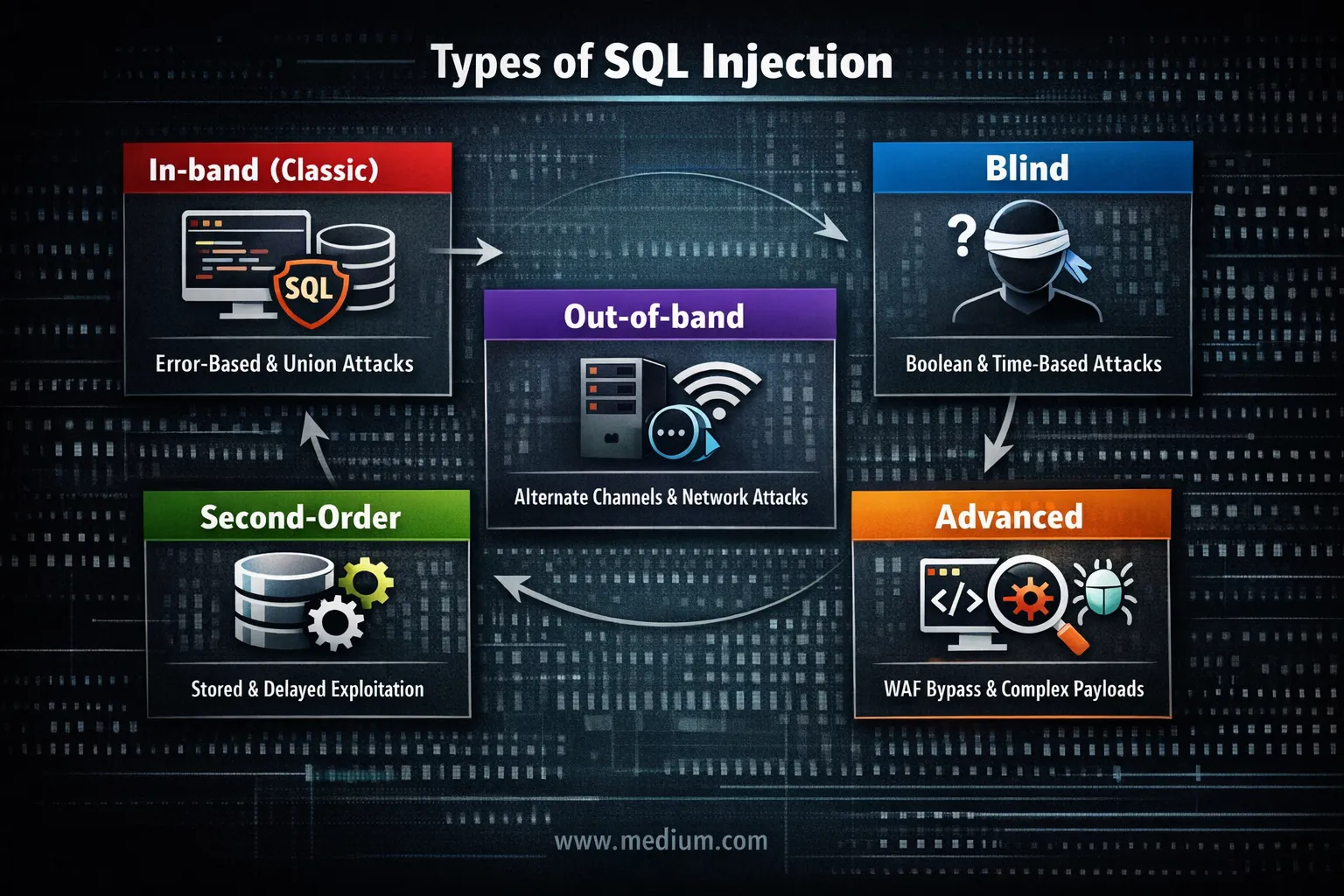
SQL Injection Guide: From Zero to Advanced Level.
In 2014, a hacker sat in a coffee shop in Moscow. He typed a single character into a search box: ' Just one apostrophe.The website exploded with an error message revealing the entire database structure. The vulnerability? SQL Injection. The same bug that existed in 1998.
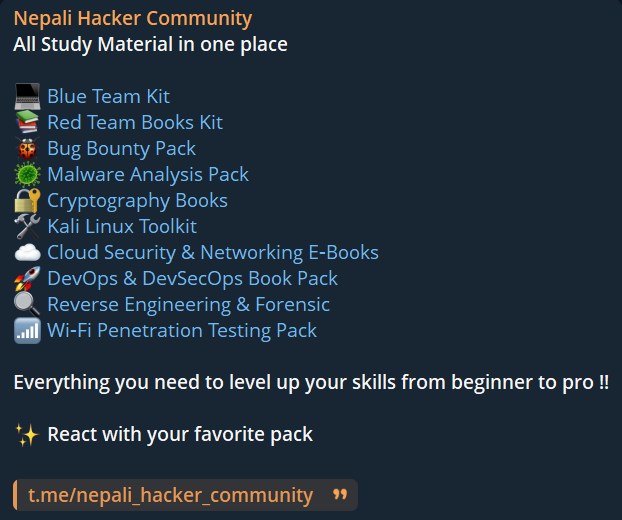
All Study Material in one place
Everything you need to grow from beginner to pro in the world of Cybersecurity.

Your Suggestion and Doubts
For any questions, support, or suggestions, feel free to email us at : Nepali_hacker_community@protonmail.com I may be slow to respond but you will definitely receive a reply. Please note: Personal questions or inquiries about the individual behind this platform will not be entertained. Transparency, feedback, and corrections are always welcome—from the heart.